Microsoft Windows has hidden an Easter Egg since Windows Vista. It allows users to create a specially named folder that acts as a shortcut to Windows settings and special folders, such as control panels, My Computer, or the printers folder. This “God Mode” can come in handy for admins, but attackers are now using this undocumented feature for evil ends. Files placed within one of these master control panel shortcuts are not easily accessible via Windows Explorer because the folders do not open like other folders, but rather redirect the user.
In the case of a recent threat variant, Dynamer, the malware is installed into one of these folders inside of %AppData%. A registry run key value is created to persist across reboots. (The executable name is dynamic.)
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
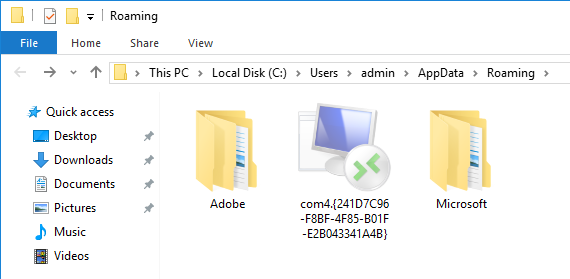
lsm = C:\Users\admin\AppData\Roaming\com4.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}\lsm.exe
This key allows the malware to execute normally, but when the folder “com4.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}” is opened, it redirects to the RemoteApp and Desktop Connections control panel item.
 The monitor icon represents the folder created by the malware.
The monitor icon represents the folder created by the malware.
 The unsuspecting user is shown a window that contains no files.
The unsuspecting user is shown a window that contains no files.
To make matters worse, the malware author has attempted to give this directory eternal life, by prepending the name “com4.” Such device names are forbidden by normal Windows Explorer and cmd.exe commands and Windows treats the folder as a device, thus preventing users from otherwise easily deleting the folder with Explorer or typical console commands.

An unsuccessful delete attempt from Windows Explorer.

Delete attempts from an admin command prompt.
Fortunately, there is a way to defeat this foe. First, the malware must be terminated (via Task Manager or other standard tools). Next, run this specially crafted command from the command prompt (cmd.exe):
rd “\\.\%appdata%\com4.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}” /S /Q
McAfee antimalware products are not fooled by these tricks; no special action is required to deal with this threat.
Malware reference information:
MD5: F2AB70F1696440CD00759D6DEFBAE54C
SHA1: a526d69c4b1d78e2bbad14c8cab4987f30aeb357
SHA256: 5fc5b16b48c8bbe1b1292282c448eb5982383f4555205e78bc2c70bd140d279c